Safeguarding Against Digital Threats: AV Signature Mechanics

Antivirus software has evolved into an indispensable weapon in combating digital threats, including malware. An integral aspect of these antivirus solutions is the utilization of signatures. These signatures play a pivotal role in the identification and mitigation of known strains of malware. In this article, we delve into the mechanics of antivirus signatures, shedding light on their creation and the process of signing malware for future recognition.
Understanding Antivirus Signatures
Antivirus signatures act as distinctive patterns or fingerprints that uniquely identify specific strains of malware. These signatures are developed by analyzing the characteristics and behavior of existing malware samples and extracting their unique properties.
To obtain a wide range of malware samples, antivirus companies source them from various channels, including online repositories, honeypots, and user submissions. These samples encompass diverse types of malware, such as viruses, worms, Trojans, and ransomware. Security researchers then employ these samples to create accurate and distinct signatures that apply to the given sample and any related variants within the same malware family.
Signature Creation and Application
To create a signature, security researchers analyze the aforementioned malware samples using automated tools and manual inspection. They examine the code, behavior, and characteristics of the malware to identify distinctive features that can be used for detection.
The analysis process focuses on identifying patterns within the malware's code or behavior. These patterns can include specific sequences of instructions, unique strings, unique URLs, API calls, file names, and many more. Researchers extract patterns they deem relevant and unique as the basis for the specific signature, while making sure the signature is as specific as possible to minimize false positives.
Signatures are then used to scan various components of a device, such as files present on disk, memory buffers, network packets and more. Once a signature matches, action can be taken to mitigate or prevent the threat, such as quarantining the file or closing relevant processes, and of course alerting the user about the recognized threat.
Case Study
To illustrate this process, let's consider the banking trojan 'Anubis,' which commonly infiltrates devices through social engineering tactics, often disguising itself as essential applications. The analyzed sample of Anubis was obtained from an online repository.
As part of the malware analysis process, researchers can inspect the actual code of the malware through decompilation. This provides valuable insights into the malware's functionality. For the purpose of simplicity, we will focus on explaining more straightforward types of signatures, avoiding delving into intricate inner mechanisms.
Here are some of the findings from code inspection:
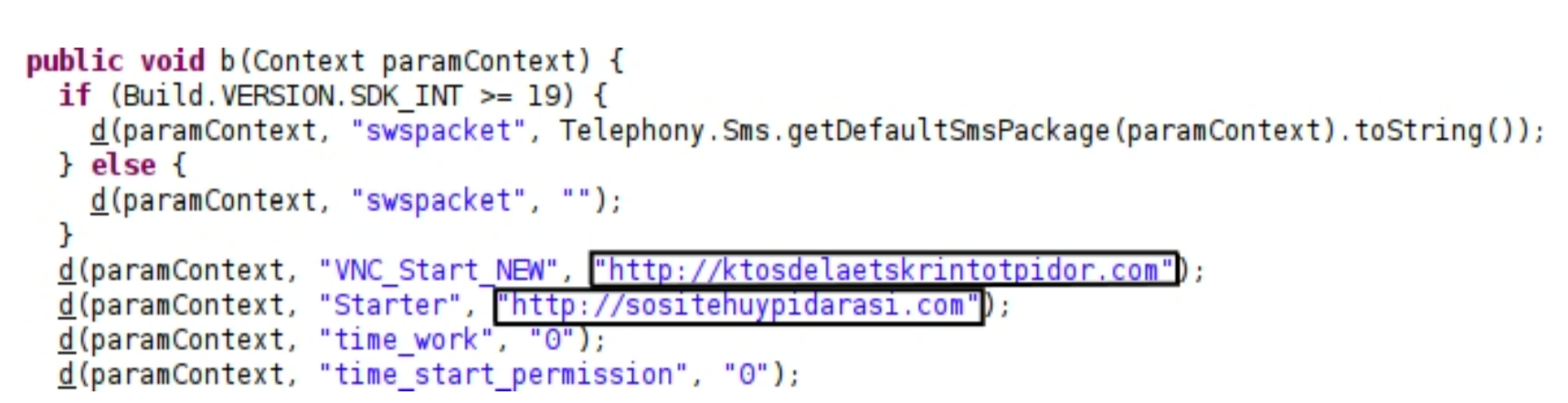
Figure 1. Unique URLs found in code
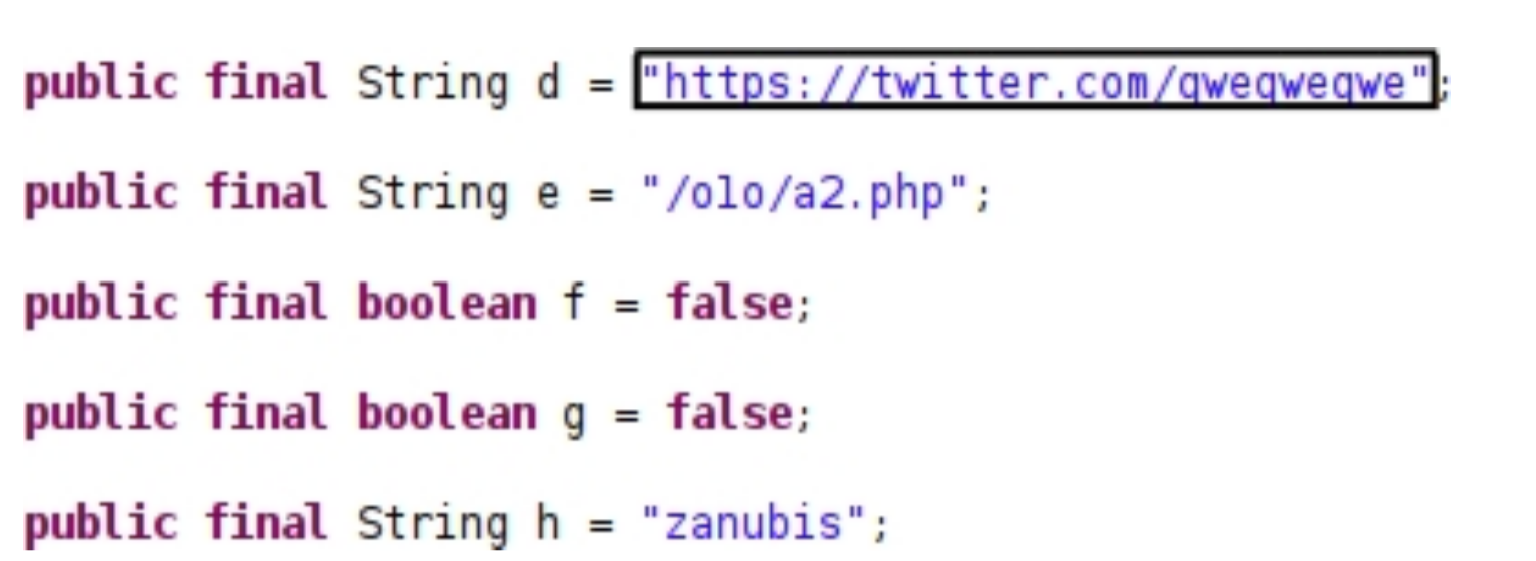
Figure 2. Twitter Account found in code
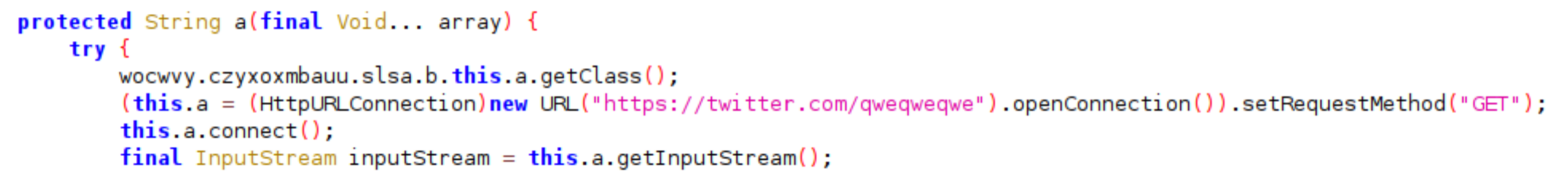
Figure 3. Malware initiates contact with the twitter account page
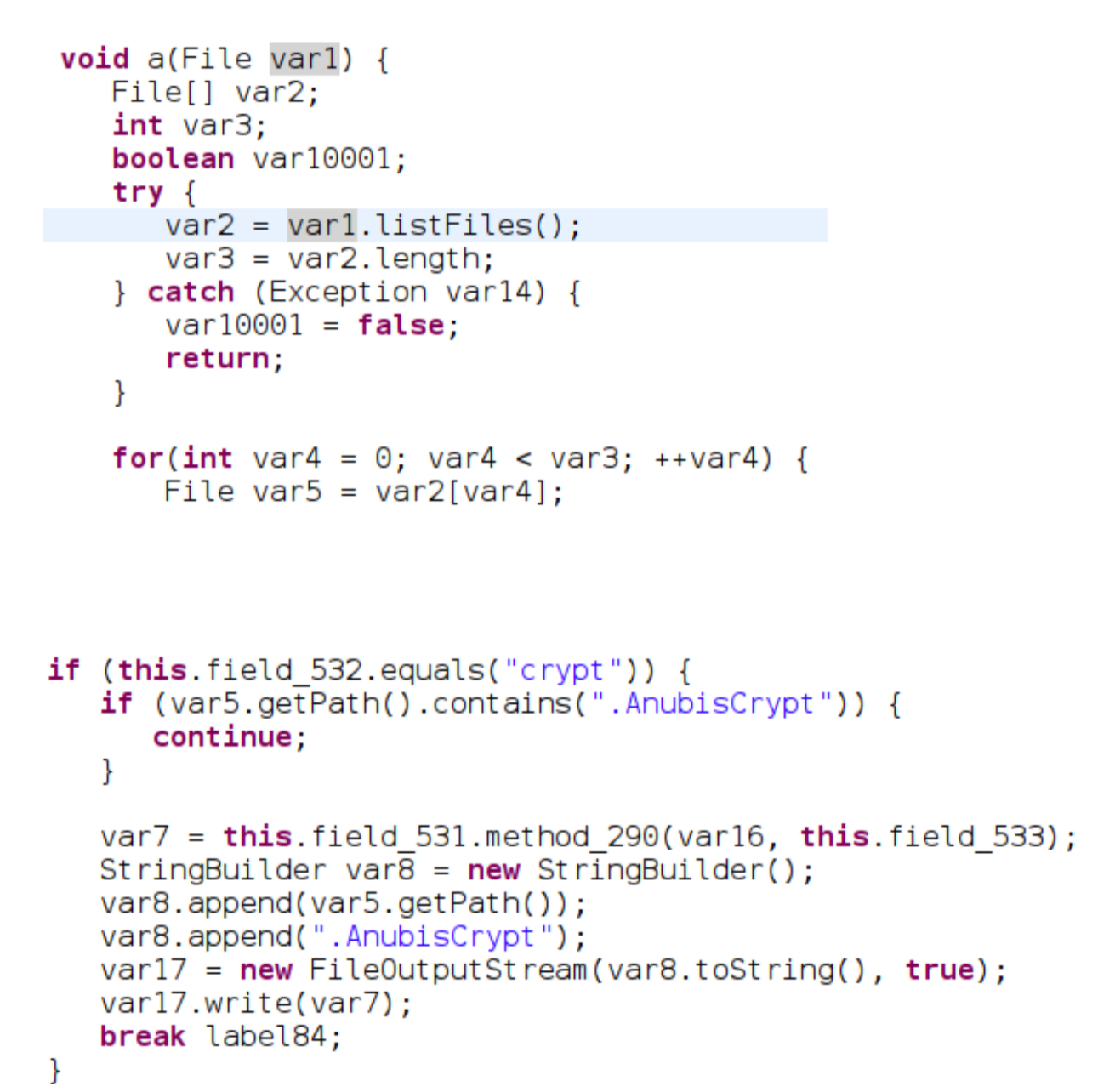
Figure 4: Code snippets of listing Files and starting a file encryption routine (method_290)
In the realm of antivirus signatures, even the simplest types can be crafted using indicators such as specific URLs found within a file, files bearing the .AnubisCrypt suffix, or monitoring HTTP requests directed to unusual destinations like Twitter.com/qweqweqwe—an action uncommon to typical applications.
As we delve deeper into advanced signature development, we encounter more intricate considerations. Figure 4 illustrates an example where a call to list files on a device is followed by subsequent calls to cryptography functions. Such behavior could serve as a strong indication of Ransomware activity.
Furthermore, entire blocks of code can be encapsulated within signatures. For instance, we can identify recurring encryption logic employed by the malware and search for instances where similar or identical mechanisms are reused.
The world of malware signatures grows increasingly complex with the rise of "sophisticated" malware strains, including polymorphic malware. The content presented in this article merely scratches the surface of this expansive subject. Nevertheless, it aims to shed light on the process of creating malware signatures, thereby dispelling the fog surrounding this intricate field.

