Mobile Critters: Part 1. Man In The Middle Attack.
Welcome to the first in our series of articles detailing the many and varied ways hackers and bad actors can affect you and your computers or smartphones. We’ll be digging into several different categories of attack, and for our first topic, we’ll look into why Man in the Middle attacks are one of the more interesting and varied techniques used by hackers.
How does the Man In The Middle (MITM) attack work?
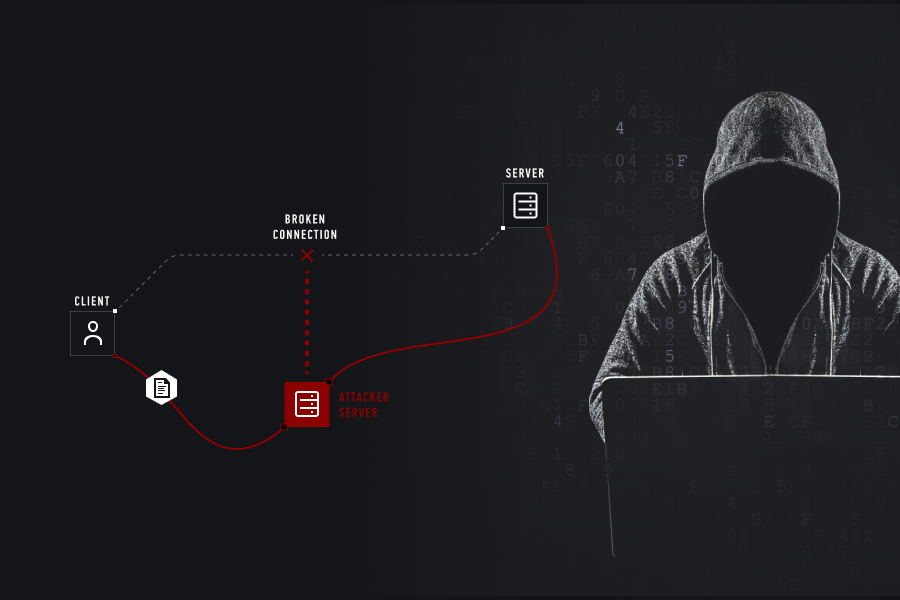
Instead of directly targeting the victim’s machine with malware or ransomware and taking control of it, a typical Man in the Middle attack (or MITM for short) intercepts the network traffic being sent to and from the device. The attacker can then capture or modify the traffic, allowing them to make copies of the data or change the information sent or received by the target. While a MITM attack can occur on any network, they are most common on public or shared Wi-Fi networks, which are often less securely configured.
The aim behind this attack may be to redirect the victim to a phishing site or malware repository or to collect sensitive information such as credentials or corporate data. A MITM usually needs the attacker to have a presence on the same network as the target, however, there are different approaches to MITM attacks depending on the access the attacker has.
Network traffic interception during Man In The Middle attack?
Network traffic can be intercepted in several ways: the attacker may have taken control of the network’s router by leveraging a vulnerability or misconfiguration; they may be spoofing the IP address of the router, making users of the network send their traffic to them instead; or they may have set up a spoof Wi-Fi network of their own for devices to connect to.
Some strains of malware also act as a MITM, sometimes referred to as “Man in the Browser”. Instead of intercepting all the traffic coming in and out of the device, they will capture just the web browsing activities and siphon them off to the attacker’s infrastructure.
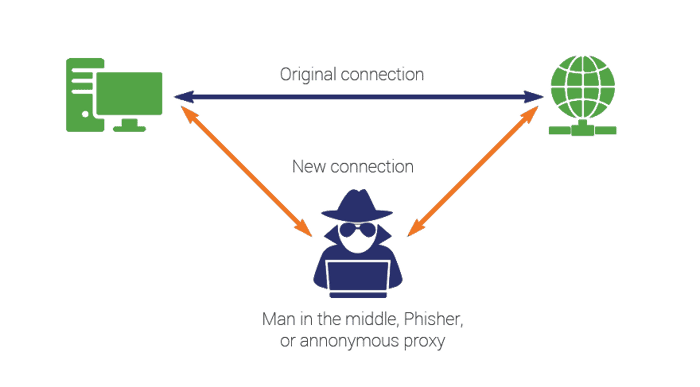
In all these situations, the attacker has visibility of traffic going to and from the target, giving them the ability to capture a copy or modify it, for example changing DNS lookup data to redirect the victim to a malicious website or capturing and modifying cookies used by the browser.
DNS server takeover during the Man In The Middle attack
Finally, another approach is to take control of the network’s DNS server or present a new DNS server for users to query. Distinct from modifying captured DNS traffic, the zombie DNS server can send a victim directly to a malicious host instead of the legitimate destination without tampering with the packets themselves.
Much of this activity can be mitigated by encrypting the traffic, and certificate-based SSL encryption is intended to provide protection against tampering with network traffic. However, the attacker may be able to carry out decryption of SSL encrypted traffic by masquerading as the intended destination and presenting their own certificate instead of the real one. Once the encrypted session is set up using their certificate, the attacker can decrypt any data being transmitted.
The best protection against MITM attacks is a VPN, which uses strong end-to-end encryption and connects directly to a secure destination. VPN traffic is much harder to tamper with as it is encrypted before sending using a pre-determined algorithm, rather than having encryption set up as part of a session with the destination. This gives an attacker little or no opportunity to read or change any network traffic they capture.

