1 WhatsApp call - that's all it takes to start spying on you.

WhatsApp calls from strangers – a new threat to your data security.
A zero-day vulnerability discovered in one of the world’s most popular messengers – WhatsApp not so long ago enables cybercriminals to eavesdrop on your conversations, read chats that are supposed to be encrypted, manipulate your microphone and camera, and moreover – install spyware to exploit other surveillance opportunities. Now WhatsApp’s users are at risk of exposing their photos, videos, contacts, and all it takes – a WhatsApp call from a hacker.
New flaw in WhatsApp
Every WhatsApp user can lose their profile at any second with a minimal chance of recovery. As mentioned in Forbes, it is simply impossible to protect against this, and an attacker will not even need to hack the gadget - he just needs to know the user's phone number, after which he can initiate the blocking procedure without the possibility of re-authorization in the system.
The ability to deprive anyone of using WhatsApp is the result of a giant vulnerability discovered in the messenger by security experts Luis Carpintero and Ernesto Canales Pereña. They notified the WhatsApp developers of their find, but they have not yet released a patch to fix the breach, leaving 2 billion users at risk of losing their account.

WhatsApp does not protect users from blocking their profile in any way.
WhatsApp is the most popular messenger in the world. According to Statista.com, in terms of the number of monthly active users in January 2021, it was ahead of Facebook Messenger (1.3 billion) and Chinese WeChat (1.21 billion) with its more than 2 billion, along with QQ (617 million). Since February 2014, WhatsApp has been owned by Facebook.
How WhatsApp vulnerability works
The vulnerability in WhatsApp allows a complete blocking of the victim's account and is carried out in two very simple stages, at each of which the performer does not even need hacking or social engineering skills - he will not contact the profile owner at all.
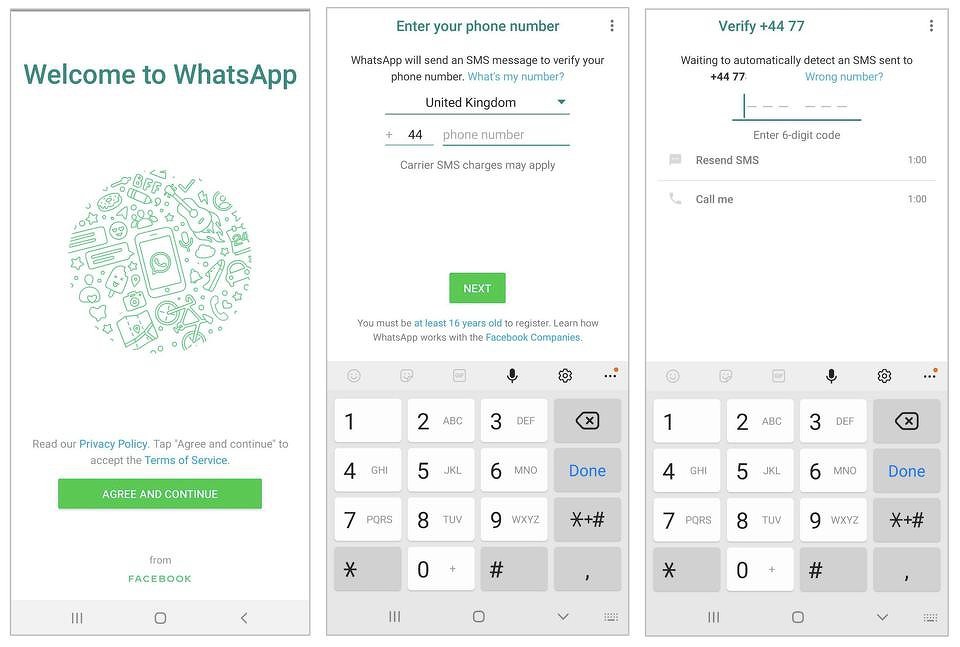 WhatsApp login window
WhatsApp login window
At the first stage, the attacker just needs to install WhatsApp on the smartphone and try to log in with the desired phone number. The messenger will send an SMS with a confirmation code to him, and here it is calculated that the owner of the number will ignore them. After several such attempts, the application on the attacker's device will report too frequent authorization attempts and will allow the next one only after 12 hours. At the same time, WhatsApp will continue to work on the victim's device as before.
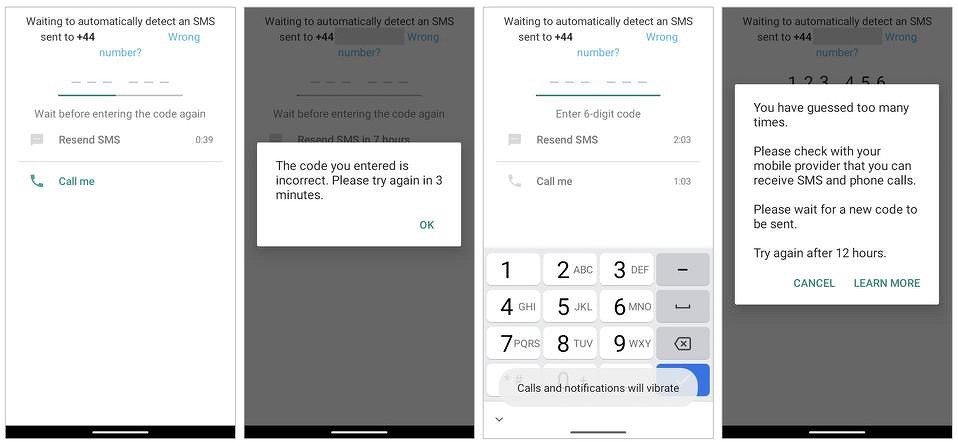 Notification about impossibility of authorization due to excessive number of attempts
Notification about impossibility of authorization due to excessive number of attempts
At the second stage, the attacker registers a new email address and writes a letter to WhatsApp technical support, in which he says that his account has been lost or stolen. He asks to turn it off and indicates the victim's number. WhatsApp can send an automated email asking you to rewrite the number, and the attacker will do so.
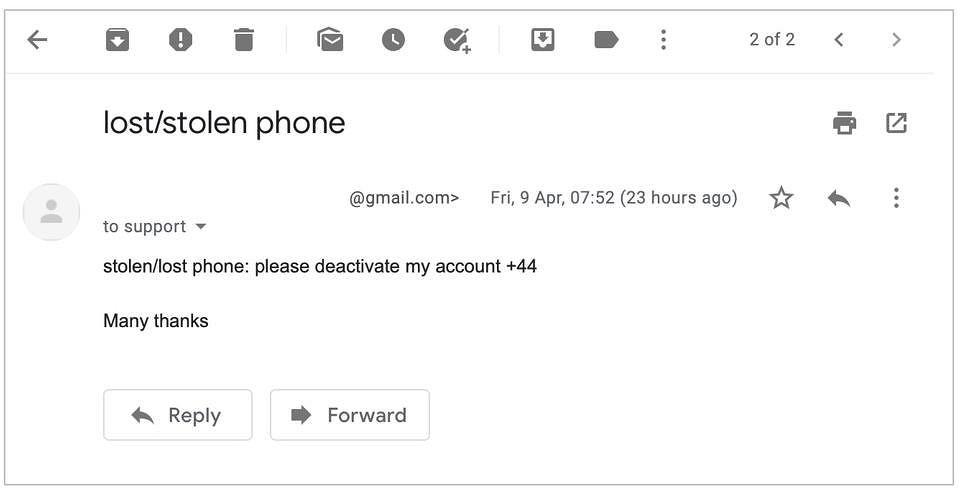 Letter to WhatsApp technical support with a request to block
Letter to WhatsApp technical support with a request to block
Further, WhatsApp, without making sure that the real owner of the account wrote to technical support, initiates the blocking procedure. After about an hour, the messenger will suddenly stop working on the victim's device - she will see a message that her number is no longer registered in the system. “It could have happened because you registered it on another phone. If you have not done so, please confirm your phone number to log in to your account again, ”the notification will say.
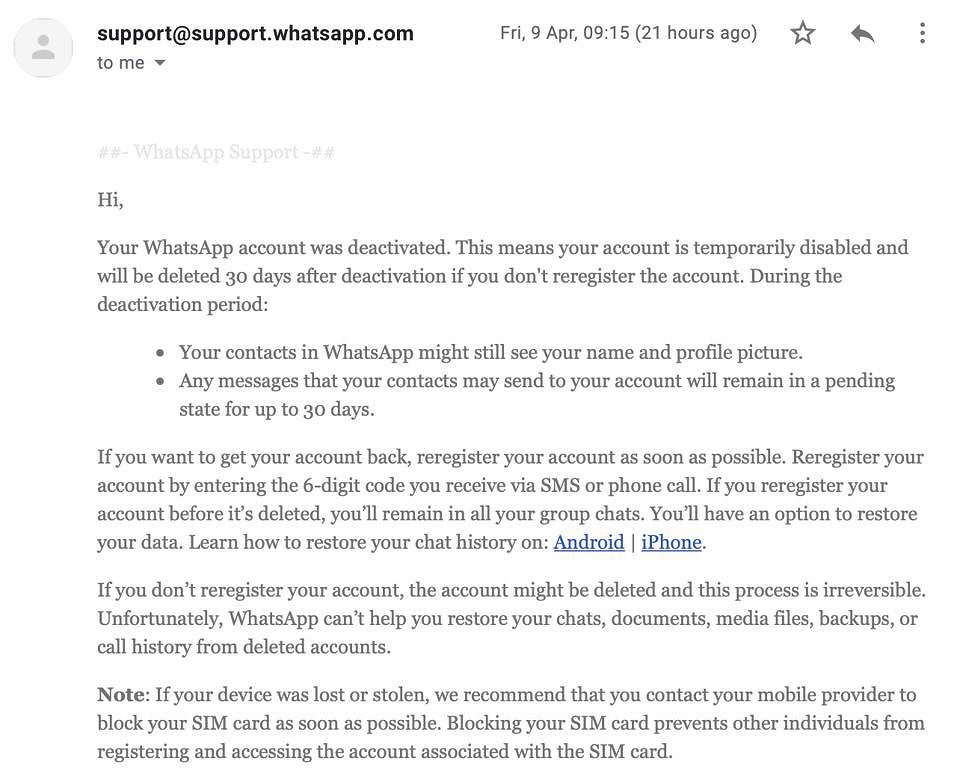 WhatsApp reply with confirmation of the request
WhatsApp reply with confirmation of the request
All of this will work even if the user has activated two-factor authentication. An attempt to request a new code will fail - WhatsApp will only allow you to do this after 12 hours.
Complete blocking
If the attacker decides to stop at the second stage, then everything will end with just the inability of the user to connect to WhatsApp with his number for several hours. After a maximum of 12 hours, the user will be able to regain control over his account and continue working in the messenger exactly as long as someone does not want to repeat the "trick" with blocking.
But in fact, there is an additional, third stage, leading to a complete blocking of the account.
In fact, this stage can become the second - the attacker does not have to send a letter in support of WhatsApp, he can simply wait 12 hours, and then again make several attempts to register someone else's number on his phone. After the third 12-hour blocking, WhatsApp will break, and instead of a timer counting down the time until the next authorization attempt, it will show "-1 second", moreover, constantly. This is a glitch in the messenger that cannot be bypassed.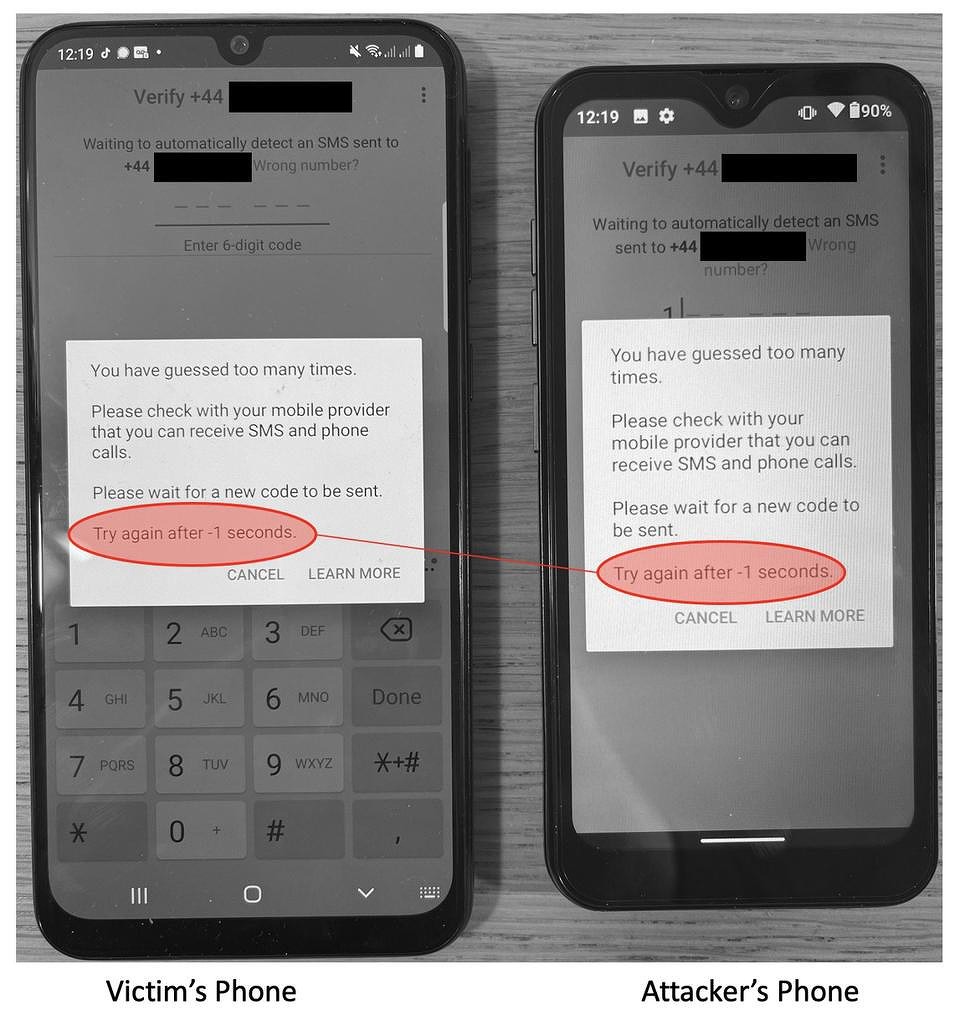
This picture will be observed both on the hacker's device and on the victim's smartphone, and as a result, no one else will be able to log in to the messenger using this phone number. The only thing that remains is to try to contact WhatsApp technical support and look for solutions to the problem.

